Open Source Intelligence (OSINT): Finding Vulnerable Systems Across the Internet with Netlas.io
- otw
- Jan 8, 2023
- 3 min read
Welcome back, my aspiring cyberwarriors!
Oftentimes, as cyberwarriors, we need to check to see whether our systems or others' are vulnerable to various known vulnerabilities and attacks. Whether a penetration tester, security engineer or other malicious actors, such information can be critical to the success of your mission. There are number of other websites that offer some insights into this key area such as Shodan and Censys but netlas.io is probably the best! In all honesty, if you are not using netlas.io, you are missing out on one of the best resources on the internet.
Netlas.io can be used in at least 5 different use cases including;
OSINT
Offensive Security
Defensive Security
Leads and contacts
Marketing Research
In this tutorial, we will focus upon using netlas.io as an offensive security tool in the context of penetration testing. The first steps of a penetration test, including reconnaissance and forming an attack surface, are faster and easier with Netlas.io. Use whois search, forward and reverse DNS search, including A, NS, PTR, MX and SPF records for network perimeter forming, scaling and attribution.
The first step is to navigate to netlas.io and create an account.

Since netlas.io is in the alpha stage of its development, it offers multiple free accounts some as simple as mentioning it on social media.

Step #2: Basic Search Query
Like many other search engines, you can build a search query with search fields and search phrases separated by a colon (:). You can search by IP address, host, whois and many other fields. In addition, you can search by sub-fields by using the field name followed by the sub-field name separated by a period.
field.subfield:value
So, if you were looking for apache web servers, you could enter;

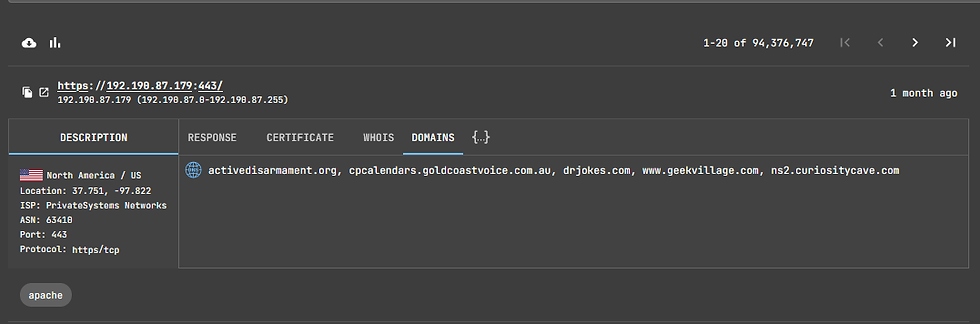
As you can see below, netlas.io was able to find 94 million servers using apache.
Each listing has a response tab, certificate tab, a Whois tab and a domains tab. When we click on the domains tab, it displays all the domains hosted at that IP address.
We can also search by host using the syntax;
host:cybrary

Step #3: Search for Vulnerabilities
One of the beauties of the site is its ability to search via vulnerabilities and cve. For instance, if I wanted to see all the sites with CVE vulnerabilities greater than 9, I could enter the search;
cve.base_score:>9

If I wanted to find all the sites will SMB enabled, I could enter the search;
smb:*

Note that in the response field, we have a sub-field "smbv1_support". We can use that sub-field to find all the sites with the flawed and vulnerable SMBv1 enabled (true).
smb.smbv1_support:true

Note that it found over 113,000 sites with this outdated and flawed version of SMB.

We can also look for sites that have a known public exploit using the search;
cve.has_exploit:*

This search reveals that there are over 74 million sites likely vulnerable to a known public exploit. To the far right of the screen you can see the CVE's of the vulnerabilities found. We can then click on the CVE tab above the listing and netlas.io will list all the known vulnerabilities. Note that the site below has 3 vulnerabilities with a severity above 9!

We can also search by the severity level of the known vulnerabilities. If we wanted to see all the sites with a severity rated "critical", we use the search term;
cve.severity:critical

If we wanted to find all the sites vulnerable to the notorious EternalBlue exploit (SMB remote code execution), we can request a search by the CVE name;
cve.name: CVE-2017-0145

Over 161 thousand sites are still vulnerable to this exploit. Just for background, here is that CVE listing at NVD.

Step #4 Using Logical Operators
Like other sites similar to netlas.io, you can use logical operators to narrow your search. You can use AND, OR or NOT (&&, ||, !, respectively). The default operator is AND.
So, if you were looking for sites running the outdated and vulnerable MySQL v5 sites with an ASN number of 4134 we could create query such as;
mysql.server.version:5 and asn.number:4134

Netlas.io also allows you to search using regular expressions (regex) and wildcards (* and ?).
Summary
If you are in the business of penetration or OSINT, netlas.io is a must have tool. It can save you hours searching for key information and vulnerabilities. I hope it goes without saying that no tool is perfect and that applies to netlas.io as well. That is why you need to become familiar with a wide variety of tools and then use the best tool for the job or situation.