Digital Forensics, Part 4: Finding Key Evidence in the Forensic Image
- OTW
- Oct 14, 2016
- 2 min read
Updated: Dec 31, 2022
In the previous articles in this series, we captured an forensic image of the suspect's hard drive, we captured a forensic image of the suspect's RAM and we had used Autopsy to recover deleted files from our first image. In this lab, we will use Autopsy to do file analysis. In order words, we will using Autopsy to find keywords, file types, metadata, etc. that may be useful in finding evidence to support our case.

Step #1
Open Autopsy and navigate to our firstimage.dd.001 file.

Autopsy will immediately begin to index this image for analysis.
When it has completed its analysis, it will then categorize each file by type. As you can see in the screenshot below, Autopsy has categorized each file type including images, videos, audio, documents, executables, and deleted files.
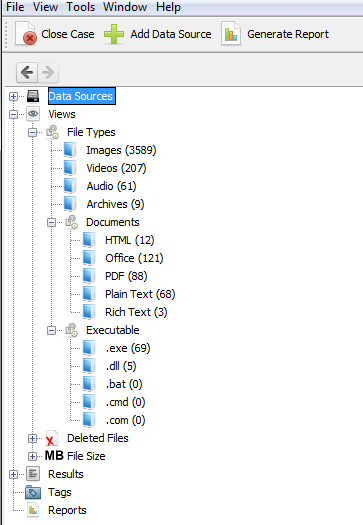
Step #2 Search for Keywords
Let's assume that we are looking for files that include the keyword "forensics". We can type this word into the Search window in the upper right of our screen and click Search.
Autopsy will now commence searching every file for that keyword. As you can imagine, in a real investigation this keyword would likely be particular to the investigation such as "ransom", "extortion", "sex", etc.
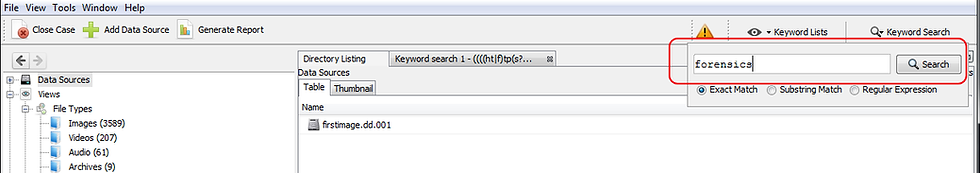
When Autopsy has completed its search, it will display each file that contains that keyword in the main Table window. We can then click on any of those file to examine it closer.
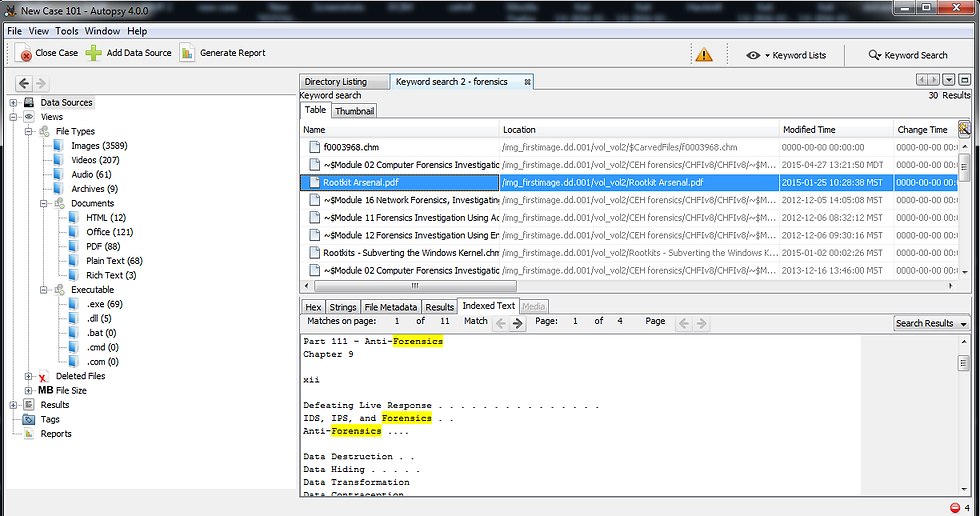
If we then click on the "Indexed Text" tab in the lower right window, it will show us every instance of that keyword and highlight it for us.
Step #3 Specialized Search Types
Autopsy enables us to do very specialized type searches that may be key to our investigation. These might include URL, email addresses, phone numbers or IP addresses.
Click on the eye near the upper right on this screen. It should open a pull down window like that below. Here we can search for;
1. Phone numbers
2. IP addresses
3. email addresses
4. URL's
Let's see if we can find any URL's in these files that may be useful in identifying what the suspect was doing before the system was seized.
In the pull down window click on the check box next to URLs. It will populate the regex expression is using to find URL's.

Next, click Search and Autopsy will begin looking through every file for that text pattern. The regular expression it is looking for is displayed in the right hand window.
Regular expression searches are very CPU intensive and slow, so be patient.
When it is done doing this search, it will display the results like below.
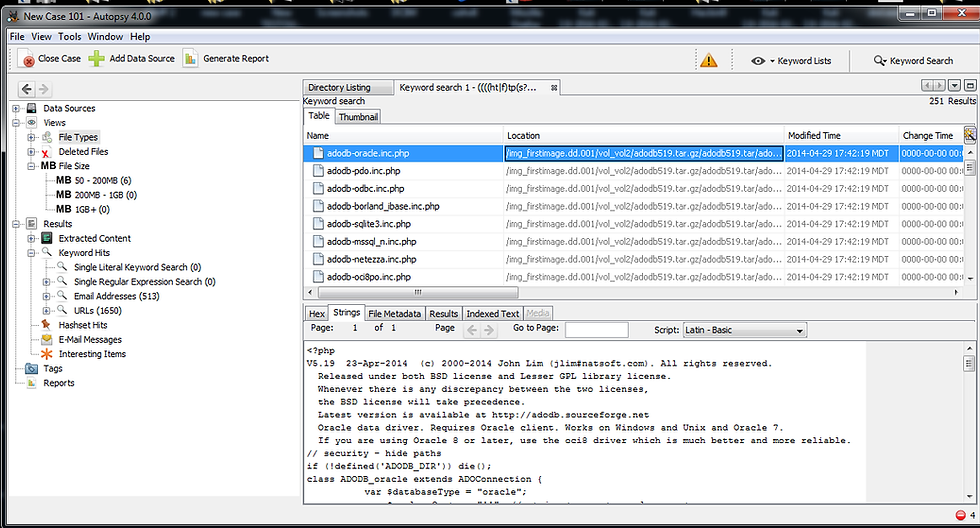
As you can see above, Autopsy displays every file that it found a URL in.
In addition, we can use this method to find email addresses as well, but when Autopsy did its initial analysis, it categorized all the email addresses it found in the Explorer pane as seen below.
Conclusion
Autopsy is a powerful tool for doing forensic image analysis. Among the many things it is capable of doing is deleted file analysis, file type analysis, keyword analysis, and finding such key artifacts as URL's, email addresses, IP addresses and phone numbers. In addition, we can create custom regular expressions to search for just about any text pattern one can imagine.