Search
Vulnerability Scanning
Vulnerability scanning is a key skill for security engineers and pentesters. It involves using tools to identify known vulnerabilities in networks or websites, serving as a standard best practice in cybersecurity.


Cyber Threat Intelligence (CTI) and Network Defenses: Getting Started with CrowdSec
Welcome back, aspiring cyberwarriors! In the ever-evolving landscape of cybersecurity, new tools and approaches are constantly emerging...
5 min read
514 views


Vulnerability Scanning: Automatic Search For Known CVEs With CVEScannerV2
Welcome back, aspiring cyberwarriors! During reconnaissance, our goal is to identify vulnerable services within our target’s network. To...
3 min read
1,311 views


So...You Thought Your VPN Was Keeping you Safe and Secure?
Welcome back, my aspiring cyberwarriors! Although VPN's are sold to keep you safe and secure online, many of them are far from from safe...
6 min read
14,056 views


Vulnerability Scanning with Nuclei: The High-Speed, Customizable Solution for Advanced Vulnerability Scanning
Welcome back, my aspiring cyberwarriors! Nuclei is an advanced, open-source vulnerability scanner that has gained significant popularity...
5 min read
1,775 views

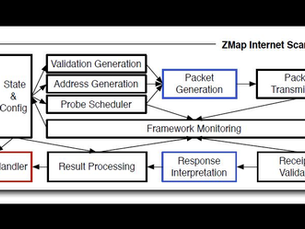
Zmap for Scanning the Internet: Scan the Entire Internet in 45 minutes
Welcome back my aspiring cyber warriors! Most of you are aware of the power of nmap and nmap scripts for reconnaissance on a target and...
4 min read
23,262 views


Reconnaissance: Scanning and DoSing with Scapy
Welcome back, my aspiring cyberwarriors! We have explored a number of packet manipulation tools here on Hackers-Arise that can be very...
5 min read
2,978 views


Port Scanning and Reconnaissance with Hping3
Welcome back, my aspiring cyberwarrior! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before...
6 min read
16,088 views


Vulnerability Scanning, Part 1: Nexpose
Welcome back, my aspiring cyberwarriors! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to...
4 min read
3,853 views


Port Scanning and Recon with nmap, Part 2: The nmap scripts (nse)
Welcome back, my aspiring cyber warriors! In my earlier post here at Hackers-Arise, I introduced you to an essential tool in the...
4 min read
3,636 views


Port Scanning and Recon with nmap, Part 1
Welcome back, my aspiring cyber warriors! Whether you are an aspiring master hacker, network engineer or security engineer, there is one...
6 min read
15,679 views


Evading Firewalls and IDS/IPS While Scanning the Target
As an outside attacker/pentester, we often have to deal with security devices that may interfere with our unfettered access to the...
6 min read
3,660 views